- VOX
- Technical Blogs
- Availability
- Securing Data at Rest with Encryption
Securing Data at Rest with Encryption
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The EU General Data Protection Regulation (GDPR) mandates that personal data protection is a fundamental right of all persons, whatever their nationality or residence. All organizations which maintain sensitive customer information such as financial services, telecom companies, defense sector, healthcare institutes must comply with new regulations contained by GDPR.
Data Encryption in InfoScale:
This blog focuses on encryption for data at rest.
The main use cases for the InfoScale Data Encryption feature are the following:
- Protect sensitive data from unauthorized access
- Retire disks from the use or ship them for replacement without the overhead of secure wiping of content.
Key Management:
Apart from actual data encryption, Key Management is an essential requirement for securing data. InfoScale supports encryption and manages keys in the following way.
Key Management Server (KMS):
InfoScale supports any KMS which conform to OASIS KMIP specifications. To use this type of encryption, the administrator first needs to configure a Key Management Server. Details related to configuration steps are described later in this blog.
The key provided by the KMS is not used to operate on actual data. InfoScale generates a key, known as Volume Encryption Key (VEK), to use for actual encryption. The key obtained from the KMS is used to encrypt and decrypt (wrap/unwrap) Volume Encryption Key. The Wrapped VEK is stored in a configuration DB for further use. This process of wrapping and unwrapping the VEK provides an additional layer of security for critical data.
Key Rotation Support:
The latest addition to this domain is support for periodic Key Rotation.
This capability enables customers to update data encryption keys periodically.
Security Compliance specifications:
InfoScale Data Encryption implementation uses Advanced Encryption Standard (AES) cryptographic algorithm with a 256-bit key size validated by the Federal Information Processing Standard (FIPS) Publication 140-2 (FIPS PUB 140-2) security standard.
Description:
Figure 1 shows a high-level view of the overall encryption-decryption process.

Usage:
To create an encrypted volume, use the new “encrypted=on” option when creating a disk group (DG).
#vxassist -g <DG name> make <Vol name> <size> <layout> encrypted=on
An option was added to the “vxdg” implementation, which marks a disk group (DG) encrypted so that volumes created in it are encrypted by default.
A new option was added to the “vxencrypt” utility for Key Rotation support.
#vxencrypt -g <DG name> rekey <Vol name>
As well, support was added for a configuration where all volumes in a DG would have the same encryption key. Such a DG can be created using the “same_enckey=yes” option.
#vxdg -o same_enckey=yes init <DG name> <Disk names…>
The use case for this type of DG is for when there are many encrypted volumes. Communication with the KMS server is significantly reduced by using this option, thus reducing the load on the CPU.
Configuration:
You can configure a Key Management Server for volume encryption by creating the configuration file /etc/vx/enc-kms-kmip.conf on the KMIP client. The configuration file must have the following information.
A sample configuration file is as follows:
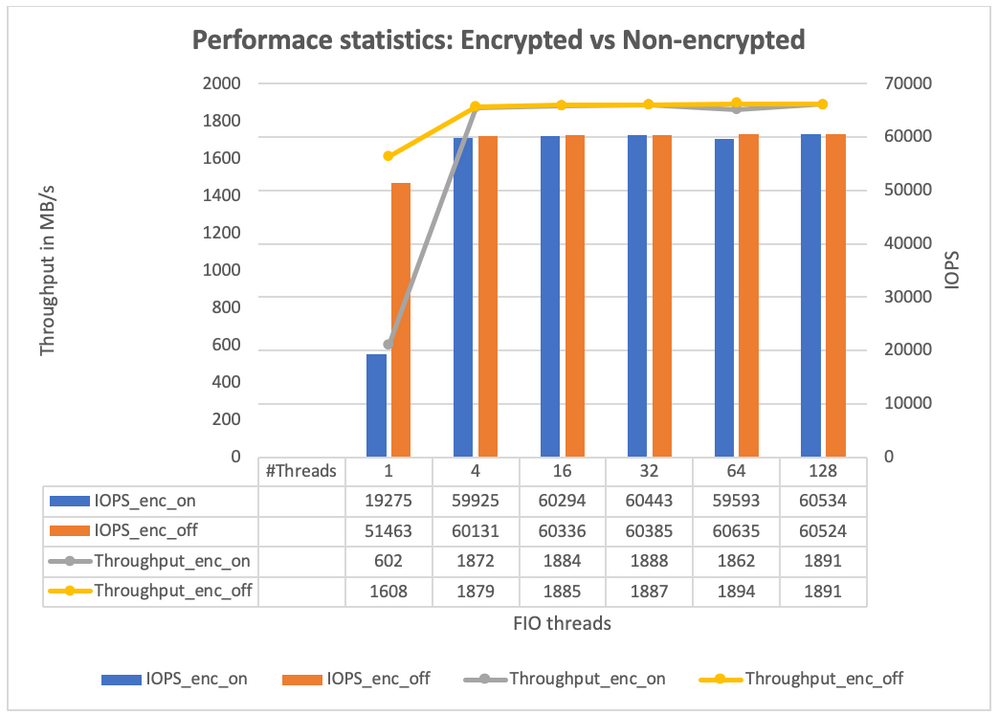
Performance statistics:
Encryption/decryption is an additional layer of operation on top of regular IO. InfoScale has designed and implemented the feature efficiently so that it provides performance similar to IO with unencrypted data.
Below are results collected for 32K size IO workload generated using the fio benchmark.
Sample FIO command:
#fio --filename=/dev/vx/rdsk/testdg/vol1 --size=500GB --direct=1 --rw=randwrite --bs=32k --ioengine=libaio --iodepth=16 --runtime=120 --numjobs=4 --time_based --group_reporting
CPU usage statistics are as below
|
|
%total_usage |
|
|
#Threads |
enc_on |
enc_off |
|
1 |
4.80 |
0.90 |
|
4 |
12.80 |
1.30 |
|
16 |
14.80 |
2.20 |
|
32 |
16.10 |
2.90 |
|
64 |
16.30 |
4.30 |
|
128 |
16.70 |
4.10 |
Recommendations for encryption
Since data encryption/decryption is a CPU intensive operation, it is recommended that servers used to perform this operation should have sufficient RAM and processing power.
It is also recommended to use CPUs designed to support Advanced Encryption Standard Instruction Set (or the Intel Advanced Encryption Standard New Instructions (AES-NI) to improve performance.
All necessary details can be found in the Admin Guide.
This is a Linux-only feature and is supported on RHEL and SuSE platforms.
Summary
InfoScale’s Data Encryption feature can provide significant benefits in helping secure your enterprise data from unauthorized access, using accepted industry standards for encryption and key management methodologies. As well, the Data Encryption feature incurs a low-performance overhead on storage IO, ensuring that your storage workloads run efficiently.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Granular Ransomware Detection in NBU 10.4 in Protection
- Securing Data and Infrastructure: A Comprehensive Approach in Protection
- Understand, Plan and Rehearse Ransomware Resilience series - Access and Improve in Protection
- Secure the keys to your data kingdom in Protection
- Illuminate Security Visibility with Veritas NetBackup Flex Appliance Security Meter in Protection