- VOX
- Technical Blogs
- Backup Exec
- Backup Exec 22.0 - Microsoft 365 Tenant Configurat...
Backup Exec 22.0 - Microsoft 365 Tenant Configuration Workflow
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Backup Exec has always been at the forefront of usability and new technology adoption. This has been demonstrated again in work done for the Microsoft 365 (M365) tenant configuration flow.
Backup Exec added support for M365 workloads with the release of version 22. Check this blog post to get an understanding of this support.
In this post let us dive deeper into the challenges faced by the team in supporting M365 tenant configuration.
Supporting M365 workloads meant many challenges that differ from supporting on-premises workloads. In such work, the “principle of least privilege” is of utmost importance, support for different and new authentication mechanism is needed, the product should never store user credentials and the flow should be automated so that the end user is not burdened with all the complexities involved in configuring the tenant.
Let us see how the team handled all these challenges.
When you run the Backup Exec tenant configuration flow, an Azure AD application is created for you. This Azure AD app is granted only the minimum required permissions, as recommended by Microsoft. This ensures that the “principle of least privilege” is honored.
All the background work of creating an application, identifying permissions, and granting admin consent for the permissions will be handled by the product, and the end-user need not have to worry about any of these things!
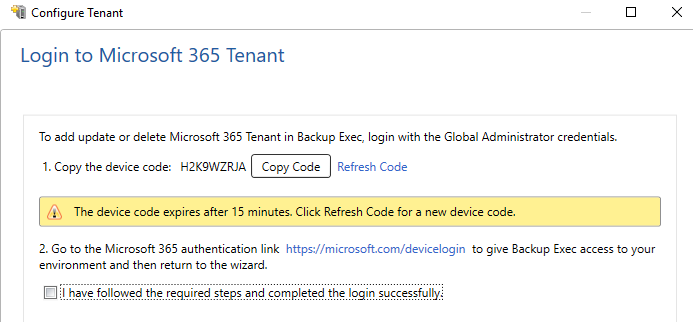
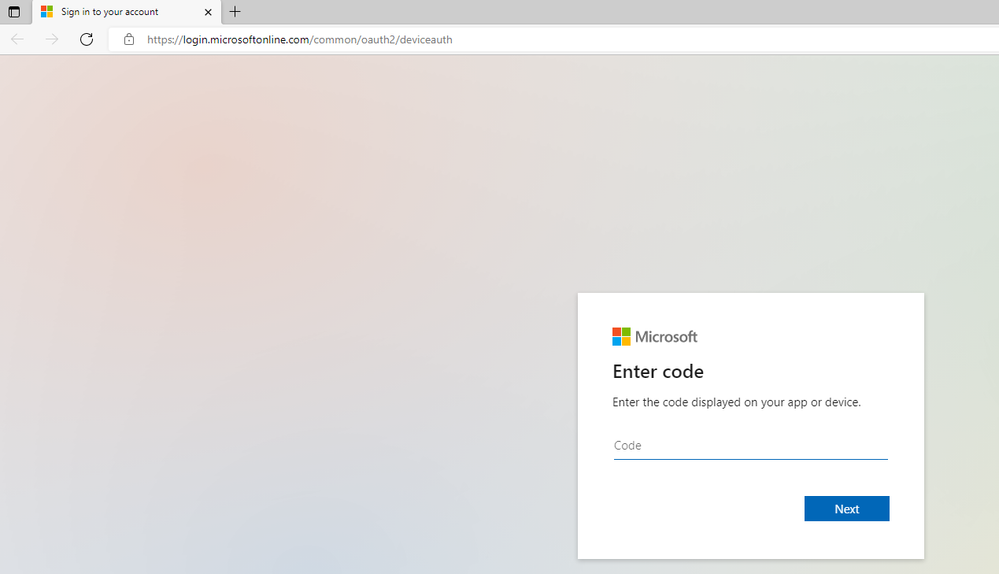
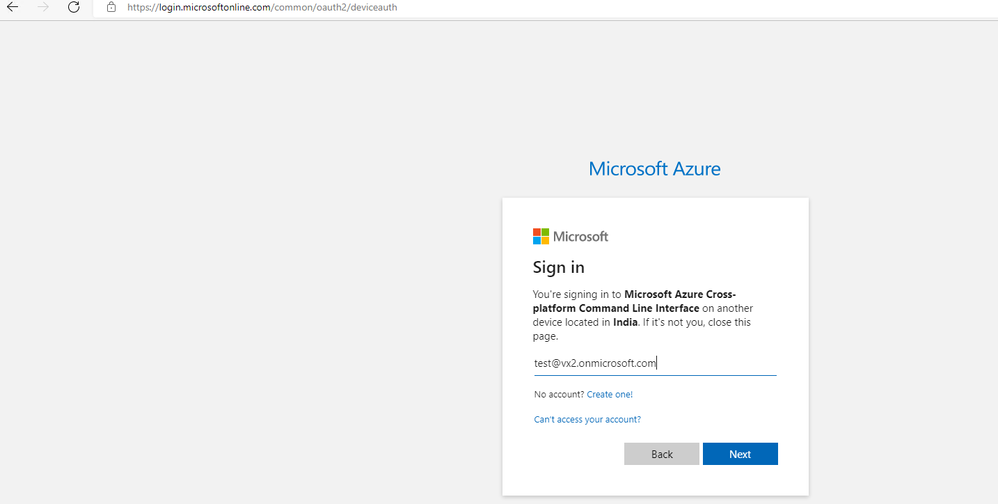
Backup Exec uses a Microsoft recommended method (OAuth 2.0 device authorization grant flow) for configuring the tenant. This will require global admin sign-in only once and only during the tenant configuration. Once the tenant is configured, then global admin sign-in will not be required again and all backup and restore jobs can run in the context of the configured Azure AD application. The global admin sign-in requirement is as per guidelines by Microsoft and Backup Exec will neither have access to the global admin credentials nor will it store these credentials anywhere.
The device code will have to be entered in a Microsoft link.
Once you enter the code you will be asked to enter global admin credentials in a Microsoft link.
Please note that the global admin credentials are needed in a Microsoft link and are not entered or stored anywhere in Backup Exec. So, you can be assured that the global admin credentials will not be used for any unintended operation!
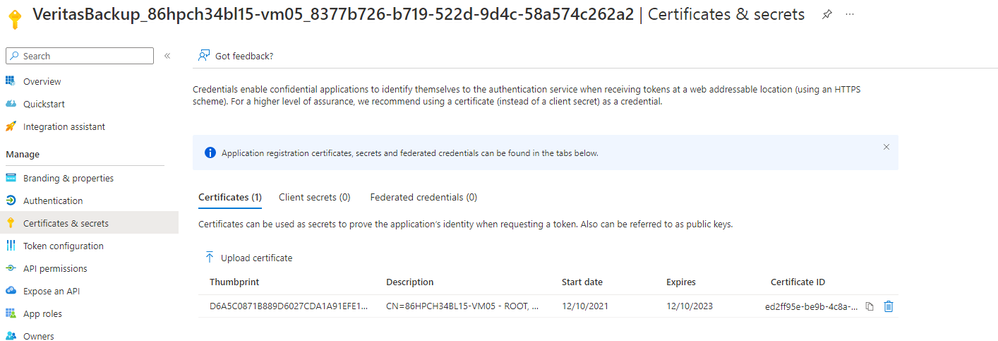
We implemented OAuth 2.0 authentication mechanism for this support. This is different from the way we support legacy username password way of authentication and a requirement for supporting many of the SaaS workloads. OAuth 2.0 protocol is a lot more secure than the legacy method. We have also added support for certificate-based OAuth 2.0 authentication which makes this even more secure.
The certificate Backup Exec generates and uses in OAuth will have a validity of only two years. This adds another layer of security. Again, all the work to generate the certificate, create a token for this work, and create, and maintain tokens for all further backup/restore jobs will be handled by Backup Exec and users need not worry about any of these things.
Users will be reminded of the possible certificate expiry well in advance and they can run the Update configuration flow to regenerate the certificate and keep the configuration up to date.
We hope all this work will save you the time needed for tenant configuration and will provide you best in class security while protecting your M365 data. Please try this out if you have not already done so and let us know your feedback!
Visit this link to learn more about what BE 22 has to offer. For details about system requirements for Microsoft 365 backups, refer this link.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Understand, Plan and Rehearse Ransomware Resilience series - Design to Recover in Protection
- Changes to Microsoft Teams Backups – What You Need to Know in Protection
- Explore Flexible Restore Options Available for Microsoft 365 Backup with Backup Exec 22.0 in Backup Exec
- Fortify your perimeter: Stop the spread of ransomware dead in its tracks in Protection