- VOX
- Data Protection
- NetBackup
- Veritas Alta Recovery Vault Short Lived Token Base...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Veritas Alta Recovery Vault Short Lived Token Based Authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2023
11:39 AM
- last edited on
04-03-2023
11:44 AM
by
JustineVelcich
![]()
Hi Friends,
Today I'd like to introduce you to the new Veritas Alta Recovery Vault Short Lived Token Based Authentication.
At Veritas, your data’s security is paramount to us, and we are always looking for better ways to secure it. With the introduction of Veritas Alta Recovery Vault for Azure in NetBackup 10.2 we introduce short lived token-based authentication to better protect your data.
Pre NetBackup 10.2, Veritas provides the ability to connect to Alta Recovery Vault cloud storage in Azure using standard credentials provided by Veritas. Enhanced security of token-based credentials further minimizes the risk window when authenticating users or devices in the NetBackup zero trust model by providing a credential management mechanism that uses short lived tokens instead of standard credentials. This new mechanism uses refresh tokens as it’s security input and generates a new access token periodically before the existing tokens expire.
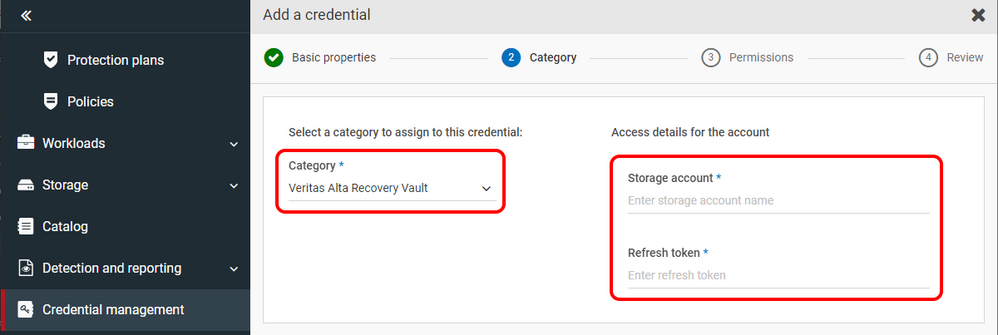
Beginning with NetBackup 10.2 users will be given their storage account and a refresh token to connect to their Alta Recovery Vault storage. Once this new information has been given a user will create a Credential in Credential Management.
Figure 1: Creating a Credential with the Storage Account and Refresh Token given by Veritas.
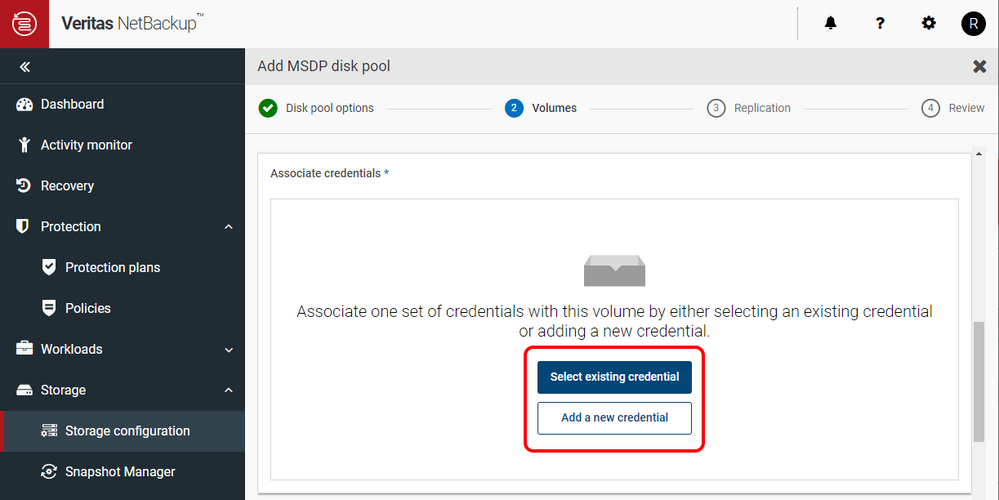
This Credential will then be selected when connecting to your Alta Recovery Vault cloud storage in Azure.
Figure 2: Selecting the existing Credential when connecting to the Alta Recovery Vault Azure storage.
Once the initial connection has been made, the Veritas Credential Management API is responsible for renewing, refreshing, accessing, and sharing access signature (SAS) tokens.
If Image Sharing and Cloud Recovery Server are desired, customers should contact Veritas Support to get a new set of tokens that can be used.
Existing Alta Recovery Vault customers can use short lived token-based authentication, but must upgrade their MSDP server to 10.2 or later and migrate their existing volume and volume containers per the Veritas Alta Recovery Vault Deployment Guide:
https://www.veritas.com/support/en_US/doc/VeritasAltaRecoveryVaultGuide
If image sharing and Cloud Recovery Server are desired, please contact your Veritas Account Team to receive tokens for the image sharing server.
Veritas Alta Recovery Vault for Azure with NetBackup 10.2 is now more secure than ever before with short lived token based authentication.
Here are some additional helpful links:
Clear Out the Clutter and Protect Your Data: Get the Most Out of Backup Storage with Veritas
Alta Recovery Vault Security Guide
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2023 05:09 AM
Hello,
We have configured NetBackup Server as planned, we have created Credentials Management entry based on the Azure downloaded txt file shared by veritas.
During the configuration of the Bucket, we used the following command lines :
[root@s-uzatas-cpx01p ~]# export MSDPC_REGION="France Central"
[root@s-uzatas-cpx01p ~]# export MSDPC_PROVIDER=vazure
[root@s-uzatas-cpx01p ~]# export MSDPC_ACCESS_KEY=XXX
[root@s-uzatas-cpx01p ~]# export MSDPC_SECRET_KEY=fdgsgfdgsfdg
[root@s-uzatas-cpx01p ~]# export MSDPC_ENDPOINT=https://XXX.blob.core.windows.net
[root@s-uzatas-cpx01p ~]# export MSDPC_MASTER_SERVER=XXX
[root@s-uzatas-cpx01p ~]# export MSDPC_ALIAS=XXX_LSU-UZATAS
[root@s-uzatas-cpx01p ~]# cd /usr/openv/pdde/pdcr/bin/
[root@s-uzatas-cpx01p bin]# ./msdpcldutil create -b xxx-bucket-01 -v xxx-vol-01 --mode GOVERNANCE --min 1D --max 1Y -l 2030-12-31 --enable_sas
Directly after that we have the following error that we were unable to fix :
{"level":"error","error":"Failed to get SAS credential.","time":"2023-08-23T17:02:07+05:00","message":"Failed
to get SAS URL credential. Please check the exported environment variables."}
{"level":"error","bucket":"xxx-bucket-01","volume":"xxx-vol-01","error":"Failed to get SAS credential.",
"time":"2023-08-23T17:02:07+05:00","message":"createVolume(): check container failed"}
Failed to get SAS credential.
Error: 141: check container failed.
We were following : https://www.veritas.com/content/support/en_US/doc/VeritasAltaRecoveryVaultGuide
Waiting for your answer.
Thank you,
- NetBackup 10.4 Gives AWS Users MORE Security Options with STS Support! in NetBackup
- Attention DBAs! New with NetBackup 10.4, PostgreSQL Recovery to PIT in Hours/Minutes/Seconds!! in NetBackup
- Sooooo…How Are You Getting Your AI Back After a Disaster? in NetBackup
- It's Time To Do This Cloud Thing! in NetBackup
- Classic Backup & Restore Luxury Comes to OpenStack with NetBackup 10.4+ in NetBackup