- VOX
- Technical Blogs
- Protection
- Fortify your perimeter: Stop the spread of ransomw...
Fortify your perimeter: Stop the spread of ransomware dead in its tracks
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Today, organizations of all types and sizes face similar problems: defending against ransomware attacks, responding to rapidly changing business environments, and ensuring they meet critical backup and recovery service level agreements (SLAs). With NetBackup 10.1, we’ve eliminated the need for additional infrastructure and ancillary software when isolating and protecting customer data from threats, while extending threat detection to modern application workloads. For more information, check the solution briefing Fortify your perimeter: Stop the spread of ransomware dead in its tracks and the Flex Appliance Isolated Recovery Environment White Paper.
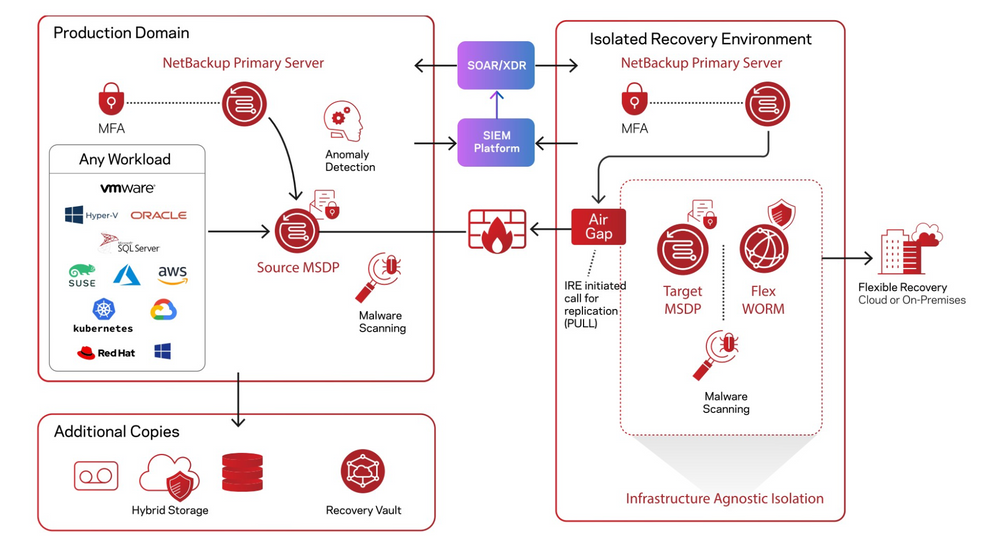
Traditional network isolation solutions physically or logically break connectivity between secure locations. Commonly referred to as the “pushing” of replication data from the source to the target, the source domain independently processes and submits a replication job to a target domain. This traditional approach limits the time available to replicate critical data into a secure environment.
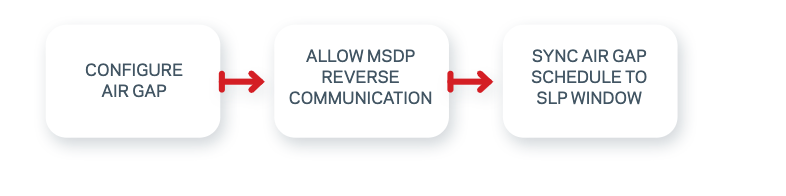
By contrast, the “pull” model pulls the replication request from the source through a specific window as defined in the IRE air-gap schedule. As of version 10.1 released last week, NetBackup’s IRE solution optimizes data movement by offering a pull replication model, where the request to send data comes from the IRE side, the MSDP reverse connection, to better control data flow and further secure the environment both logically and physically. NetBackup’s Isolated Recovery Environment minimizes threats from ransomware and rogue users by:
- Storing an isolated copy of the data, ensuring it stays unaltered until it is no longer needed
- Detecting ransomware within the protected data to prevent reinfection when restoring data
- Providing scalable recovery operations, so business services can meet service-level objectives
- Enabling predictable recovery processes that can be rehearsed to on-premises or cloud infrastructures
NetBackup Malware Scanning and Anomaly Detection
NetBackup Malware Detection provides additional control in the detection and recovery portions of the workflow. NetBackup offers two malware scanning methods to protect your data’s integrity and the backup image: on-demand scans and scans automatically triggered by high anomaly scores.The integrated NetBackup malware engine allows you to perform on-demand scans of backup images for latent threats. Additionally, integration with leading malware scanners such as Microsoft Defender and Symantec Protection Engine were made available in the NetBackup 10.0 release. Storing the scan’s status in the NetBackup catalog empowers you to restore confidently with visibility into the malware scan status. Add your malware scanning engine to NetBackup for added resistance to the growing cyber-terror threat .
An IRE that is Flexible and Easy to Set Up
You can configure an isolated recovery environment (IRE) on a NetBackup BYO media server or Flex Appliance WORM Storage server to create an air-gap between your production environment and a copy of the protected data. The air-gap restricts network access to the data except during the timeframe when data replication occurs, providing further protection against ransomware and malware. To configure an IRE, you need a production NetBackup environment and a distinct NetBackup IRE environment with an MSDP server configured. The production environment does not require any additional steps for this feature. Enabling IRE functionality is performed within IRE itself, desinating trusted sources and a schedule.
Veritas continues to strengthen NetBackup’s Isolated Recovery Environment controls to easily secure a replication target from ransomware and malware. With NetBackup’s granular controls for an IRE and the SLP operations, you no longer have to sacrifice your organization’s security posture for data flow.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Power-up ransomware resiliency with retention lock/WORM in Protection
- Fortify your perimeter: Stop the spread of ransomware dead in its tracks in Protection
- Protecting Healthcare and Critical Infrastructure from Modern Malware in Protection
- NetBackup Flex release 2.1 adds resilience to the Appliance Multi-Layer Immutable Architecture in Protection
- How Traditional Data Protection Strategies Increase the Risk for Your Business in Partners