- VOX
- Technical Blogs
- Protection
- Securing Data and Infrastructure: A Comprehensive ...
Securing Data and Infrastructure: A Comprehensive Approach
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Security of data and infrastructure has become a world in itself. Everyone talks about so many terms that it’s easy to feel overwhelmed by the possibilities of securing your data. At the same time, you may wonder what you need in your environment and whether it is going to be enough.
I hear so many terms get thrown around like anomaly detection, multifactor authentication, malware scanning, zero trust access, etc. But what am I really protecting, and am I covering all my bases to make sure that my data and infrastructure are protected? How can I tell with confidence that I have a good security strategy?
One good way I have found to answer that question is to narrow down my focus and compartmentalize the areas that I need to solve for. First and foremost, I need to figure out what my attack vectors are. Once I figure that out, I have a finite number of vectors that I can easily comprehend and think about securing.
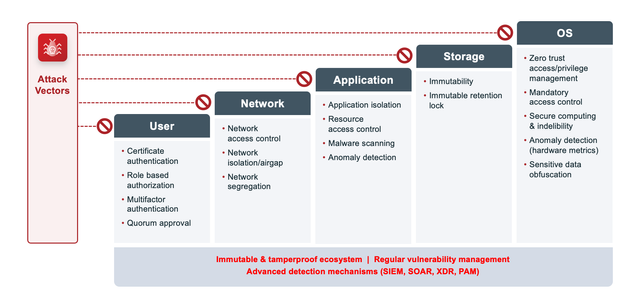
As a part of that exercise, I came up with my five attack vectors, which are:
- Users
- Network
- Application
- Storage or data
- Operating systems
Physical hardware security could be the sixth one, but I am going to park that as something that is likely already covered, maybe because you have your infrastructure within a secure data center and in a locked cage with cameras around.
Diagram 1: Attack vectors and security needs
Once I have determined my attack vectors, I can now focus on securing those five areas against any type of attacks. I must also consider multiple ways to protect any single vector in case any of the mechanisms get breached or compromised. For example, I can have an industry-standard authentication mechanism but also use multifactor authentication in case my credentials are compromised. I can also use quorum approval or multiperson authorization for any critical operations in case someone gets access to the system.
Similarly, on the data front, I need immutability, which prevents data from being modified. I also need indelibility with my operating system to make sure that data cannot be deleted.
You can go as deep into any attack vector as needed, depending on what your requirements are for making that vector secure. I found this framework very useful in defining my requirements to secure the data and the infrastructure in a data center.
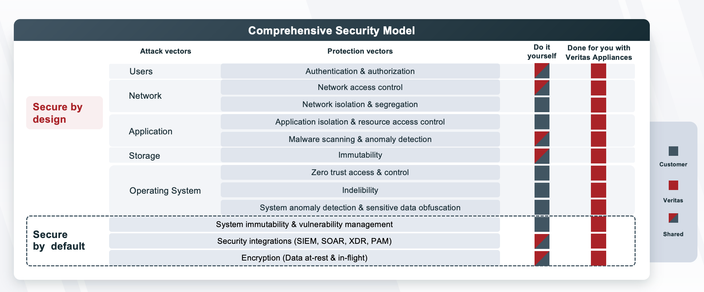
Diagram 2: Responsibility model for Security
Once you have identified the different attack vectors and needs across those vectors, your next task is to figure out how to get these requirements met in your environment. For example, you might have to go with external vendors for password and access management, for authentication, or for malware scanning and anomaly detection.
Unfortunately, not everything is available with third-party integrations. Especially when you try to protect the fundamental operating system layer, you can’t do much by yourself. For example, the system that controls access to the data needs to be immutable in architecture and indelible by design. If someone gets root access to a system, they can easily go and destroy the data.
So, you must implement these design principles on your own to get end-to-end protection and true immutability and indelibility. Concepts like zero trust access, removing root privileges, immutable architecture, managing containers, and network and application isolation are all needed to get that end-to-end protection. However, it’s complex and time consuming to do on your own.
Another big lift is vulnerability management. Given that the infrastructure now gets hit by ransomware attacks every second, the attackers look to expose every vulnerability on any system. Managing these vulnerabilities and getting their fixes can be a tall order. It’s no secret that securing your environment is a team effort that requires a group of security experts who can provide ongoing and continuous protection against a 24-7 team of hackers.
That is where Veritas NetBackup Flex appliances are your natural partners, providing the end-to-end security in your environment. With Flex Appliance, you get the zero trust-based immutable architecture out of the box, plus continuous management of vulnerabilities that you wouldn’t otherwise get by just putting a data protection software on your own systems.
Read more on NetBackup Flex Appliance here.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Granular Ransomware Detection in NBU 10.4 in Protection
- Reinventing NetBackup Operations with NetBackup IT Analytics in Protection
- Illuminate Security Visibility with Veritas NetBackup Flex Appliance Security Meter in Protection
- Simplifying Protection for Telco Cloud Platform – Veritas NetBackup Delivers in Protection