What's New in NetBackup IT Analytics 11.3
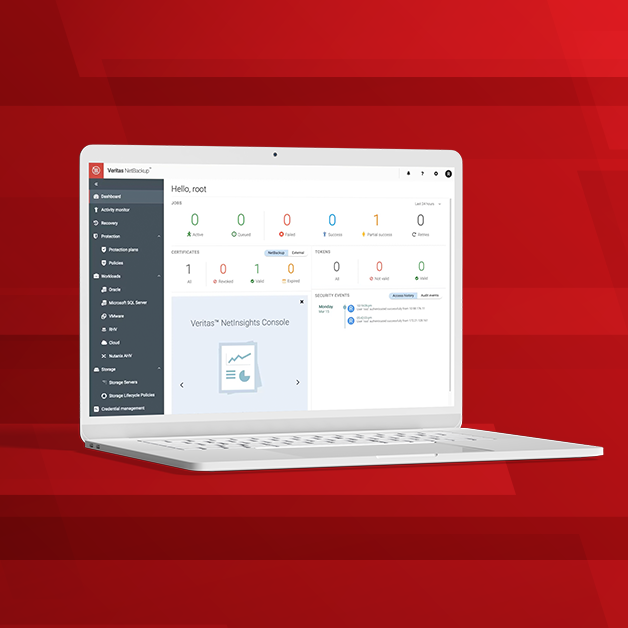
The latest release of Veritas NetBackup IT Analytics 11.3 became generally available on December 4th, delivering powerful new ransomware and security improvements alongside simplification and supporta...

The latest release of Veritas NetBackup IT Analytics 11.3 became generally available on December 4th, delivering powerful new ransomware and security improvements alongside simplification and supporta...

In a recent Data Risk Management report, 65% of surveyed executives and IT practitioners expressed that they have experienced a successful ransomware attack over the past two years (The State of the M...

With current cloud workloads expected to double within the next 12 months, more than 50 percent of enterprise organizations have adopted a cloud-first strategy. And due to the pandemic, this trend is ...

With the latest release of NetBackup 10 with Cloud Scale Technology, a host of new features deliver the most comprehensive backup and recovery solution to date. Amongst the features now available are ...

Kubernetes has become the de facto container orchestration tool for many organizations along with other distributions based on Kubernetes, such as OpenShift, Rancher, Google Container Service (GKE), A...

Organizations today are evolving their infrastructure to minimize cost while maximizing security, simplicity, and agility. Kubernetes has emerged as the leading solution, providing the benefit of cont...

Today’s cloud providers know that availability and resilience are key concerns organizations have when making decisions about migrating their data to the cloud. But these same cloud providers have als...

Over the past few years, the new paradigm of working remotely has made businesses rely on remote collaboration tools more than ever. Microsoft Teams usage, in fact, has increased to more than 75 milli...

Do you have a Hadoop cluster running with High Availability, multiple nodes, or SSL & Kerberos authentication enabled? Do you want to protect your Hadoop environment using storage, Dedupe & performanc...

The explosive adoption of SaaS solutions has not only resulted in a larger number of users, but also a larger number of SaaS applications and platforms to choose from. Oh, decisions, decisions, but ki...

Organizations around the globe are shifting their legacy IT infrastructure and workloads to the cloud. With the increased adoption of cloud apps like Microsoft 365 (formerly Office 365), Box, Slack, e...

Database administrators support a company's most business-critical applications – databases. They are accountable for ensuring their availability, and because of the mission-critical nature of the job...

At the end of February, Veritas announced the arrival of NetBackup 10, which brings many advanced features to the product and provides more support for moving backups to the cloud. Along with that, Ve...

During this year's Conquer Every Cloud event, Veritas announced our new Cloud Scale Technology based on the NetBackup 10 next generation architecture. NetBackup 10 is the first cloud-optimized, at-sca...

Cloud is an amazing technology; it opens the door to things that weren’t possible just a few years ago. The ability to host a company’s mission-critical applications and data without the need for a da...

Many exciting announcements were shared at Conquer Every Cloud 2022, and we are excited for you to get to know the people and the passion behind Veritas, with the Meet the Innovator series. It introdu...

Today, cyber resiliency and the threat of ransomware attacks are top concerns for every industry throughout the globe. According to the 2022 SonicWall Cyber Threat Report, researchers observed 623.3 m...

Creating an entire NetBackup architecture in the cloud has never been easier. Now, with Google, bring your own Google Cloud license (BYOL) to deploy your NetBackup Primary, Media, or CloudPoint server...

In partnership with Amazon, Veritas has created a Bring Your Own License (BYOL) based solution to deploy a NetBackup Primary, Media, and/or CloudPoint server(s) from one simple template. It’s never be...

In partnership with Microsoft, Veritas has created an Azure Resource Manager (ARM) based solution to deploy a NetBackup Primary, Media, and/or CloudPoint server(s) from one simple template. It’s never...

It has never been quicker or easier to gain visibility into the protected workloads that are critical to your business. Automated visualization of your capacity usage and entitlements enables you to f...
Challenges There are so many trends and challenges that IT professionals are faced with today. Containers, micro-services, compliance, security, and many more. Hyperconverged is an interesting trend i...

As a customer who is deploying and hosting her own data protection software, the last two things she would want to do is (a) remember to account for configuration and customization of data protection ...

When it comes to recovery, there are two important things to think about: your recovery point objective (RPO) and the recovery time objective (RTO). These metrics define the recovery abilities for you...

Most modern enterprises tend to be heavily virtualized, from hundreds of Virtual Machines (VMs) on-premises to thousands of VMs blended between clouds and the data center. The ability to spin up VMs o...

It seems that you can’t avoid news stories on ransomware attacks these days. A couple of months ago, the University of Portsmouth campus in the UK was closed due to a possible ransomware attack on its...

Elias AbuGhazaleh | @EliasA Staff Product Manager Biography Elias has been working on data protection since 1991 and is currently the Customer & Partner Engagement Program Lead, and the Employee Resou...

Enterprises are under attack, and the ability to protect against ransomware does not only include defense strategies focused solely on the perimeter. As an attack evolves, it can move laterally across...

It is no secret that enterprises are concerned with ransomware. Every day we read about companies who have been hacked, and their data has been held for ransom or threatened with exposure of sensitive...

Organizations continue to evolve their infrastructure and look for cost-effective, agile, and secure solutions. Much of the latest phase of IT transformation has been the accelerated adoption of Kuber...
