- VOX
- Data Protection
- NetBackup
- New Critical MSDP Security Functions Get Multi-Per...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
New Critical MSDP Security Functions Get Multi-Person Authorization (MPA) in NetBackup 10.4 API
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2 weeks ago
Let’s face it, you’re far more likely to be hacked through an OS shell than a GUI, so NetBackup 10.4 safeguards MSDP shell WORM functions with MPA. This is part of our continual hardening of NetBackup as the nightmare of malware and ransomware continues to grow. NetBackup previously allowed administrators to use MPA for Web UI actions, but not shell actions. In version 10.4, we’ve added key features to help administrators secure their MSDP data assets at the shell level. These new features will help administrators stop MSDP mistakes and mischief before it can start via command line, or the NetBackup API.
MSDP User Account Management
MSDP uses the login account “spws” (with a group spwsgrp) to create and manage MSDP resources. Administrators can now define any OS-valid username and password for this account. This way, there is no known default user account name for hackers to attack to access MSDP resources.
MSDP User Shell Action MPA Ticket Creation
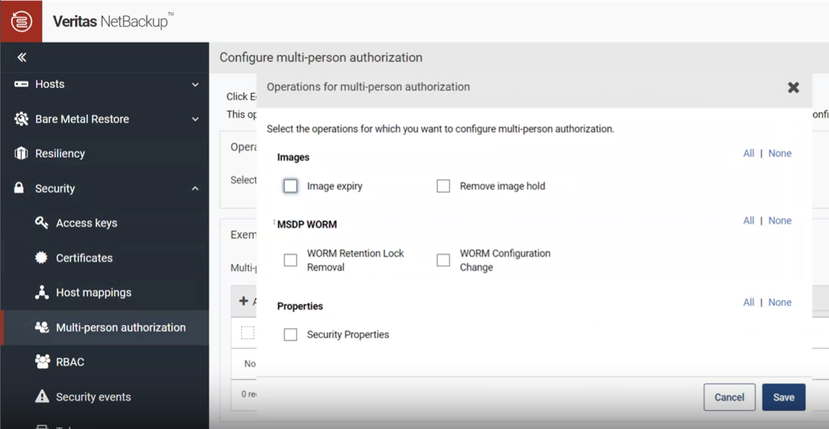
MSDP shell actions now generate an MPA ticket in the NBU Web UI for administrator review and approval or denial. Administrators simply enable these MSDP protections as shown in this figure:
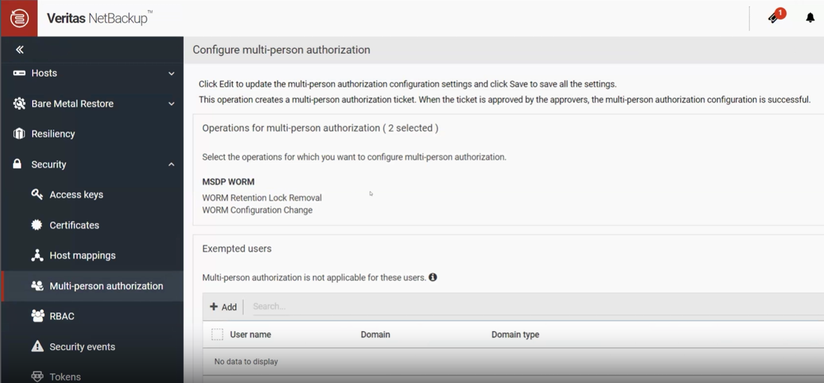
Once enabled, these protections will be shown as part of your ongoing MPA configuration as shown in this figure:
Here’s an example of how this protection works. Let’s say a valid user tries to disable WORM protection on a key backup image using this MSDP shell command, or through the API. Note how they’re warned that this function is protected with MPA. Not only does the command fail, but that if they want it to work the user has to allow a ticket to be created so that another administrator can approve the command:
[msdp-prompt} msdp-host1 > retention policy disable backup_id=somehost.media1.someplace.com_1704350028 copynumber=1
WARNING: Are you sure that you want to disable retention lock for the backup ID?
>> Do you want to continue? (yes/no): yes
Multi-person authorization is enforced. This operation requires authorization from the primary server: primary.someplace.com
Create a ticket for approval (y/n)? y
Ticket comment: some comment
Ticket 46 is created. Please wait for an approval and run the command again.
Operation failed
[msdp-prompt} msdp-host1 >
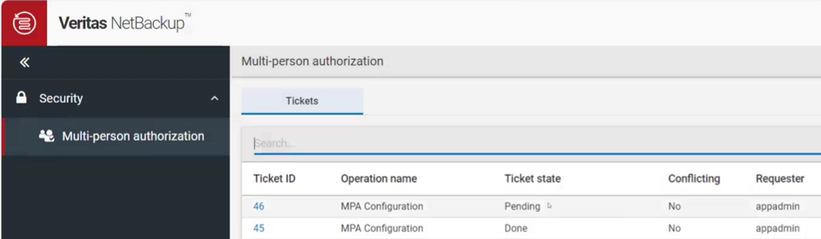
At this point, an administrator with proper permissions can review and approve/disapprove the ticket. MPA tickets form a queue which administrators can monitor for all MPA-protected actions. The above command’s ticket 46 shows up in the queue like this. Note that it’s in a pending state awaiting administrator action:
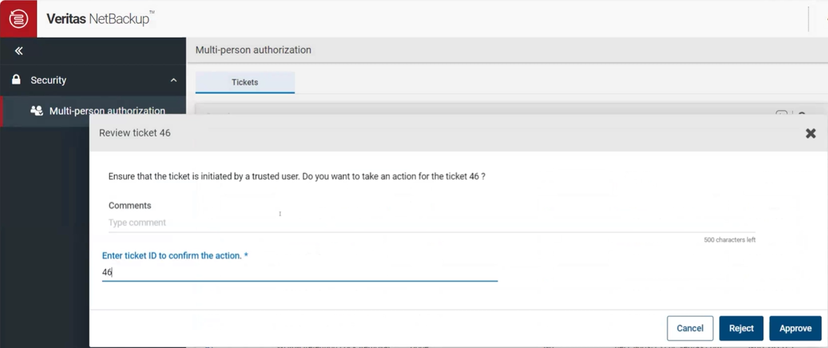
Let’s say the administrator knows this action is part of the scheduled change control, or part of some other valid image maintenance. They can approve the ticket as shown here:
Let’s also say that the user who initially ran the command knows that official policy is for all tickets to be approved or disapproved in 30 minutes or less. To be safe, the user re-runs their command again at 30 minutes and this time it succeeds like this:
[msdp-prompt} msdp-host1 > retention policy disable backup_id=somehost.media1.someplace.com_1704350028 copynumber=1
WARNING: Are you sure that you want to disable retention lock for the backup ID?
>> Do you want to continue? (yes/no): yes
Multi-person authorization is enforced. This operation requires authorization from the primary server: primary.someplace.com
Ticket 46 for this operation is approved.
Disable image retention lock success.
Operation completed successfully
[msdp-prompt} msdp-host1 >
If say a hacker using a non-existent or invalid account tried to run the operation immediately, the approving administrator would see a message to that affect when they reviewed the ticket. Any obvious hacking attempt is then flagged at the reviewal stage of the ticket, and therefore shell stage of this command.
MSDP User Shell Auditing and Reporting
Version 10.4 shell auditing has been hardened as well. Users and their Security staff wanted two key features for auditing shell user activities. These features work quietly in the background so most users won’t even know they’re there. However, they’ll be constantly documenting a trail of activities for IT Security and Administrator staff:
- Record the actions performed by a shell user (malicious or not) by adding their actions to the shell syslog. These actions can then be alerts forwarded to an external SIEM/XDR platform
- Have a command history audit trail for Security staff to verify what commands/steps were performed by logged in users
These two features were implemented as follows:
- For FLEX systems, the VXOS container OS shell now has auditing for WORM container activities. Any attempt to alter WORM configuration or status generates alerts that can be reviewed and forwarded to SEIM/XDR platforms
- In general, any command typed at the MSDP WORM shell is audited into the syslog. It is no longer possible to use MSDP WORM commands without generating an audit trail
Conclusion
NetBackup administrators should partner with their organization’s Security team(s) about using these great new features. Most security teams won’t be aware of these features and their usefulness to their reporting efforts. The NetBackup team should forward this information to them as soon as NetBackup is at version 10.4 or higher.
- NetBackup 10.4 MPA and MFA Enhancements --- Modern Security for Modern Times in NetBackup
- NBU API: add client into policy issue in NetBackup
- NetBackup 10.3+ MFA Container Logins and MPA Destructive Action Control in NetBackup
- Windows Netbackup 9.1.0.1 Authorization Service wont start now after server went down. in NetBackup