- VOX
- Technical Blogs
- Protection
- Power-up ransomware resiliency with retention lock...
Power-up ransomware resiliency with retention lock/WORM
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
“Data is the new oil”, which is why data protection becomes crucial for organizations, government, and businesses.
Backup Exec, a leader in the small to mid-size business segment is aligned to its commitment to have a ransomware resilient environment and to meet regulatory compliance. Backup Exec with WORM supports intelligent features such as reporting, load balancing, data lifecycle policies, managing backups, setting retention policies, and performing recovery operations from a unified Backup Exec console.
The Retention Lock or WORM (Write-Once-Read-Many) lock plays a pivotal role in data protection. It provides file or image immutability and secure data retention capabilities. Object cannot be deleted or overwritten for the duration defined by customers.
The key advantages which WORM enabled backup provides:
- Immutability: Data once written cannot be altered. This protects from accidental modifications, unauthorized changes, and even sophisticated cyber threats.
- Data integrity and resilience: With WORM-enabled backup, data cannot be altered and retains its integrity. This is crucial for compliance with regulations.
- Protection against ransomware: Data can be recovered from a secure and immutable backup set even when your primary system is compromised.
Customers can now take the backup in cloud with WORM enabled backup set even in cloud with governance as well as compliance mode. Governance mode can be used when you want to protect objects from being deleted by most users, “root” users can have special permissions to alter the retention settings or delete the objects. Compliance mode can be used if you have a requirement to store compliant data. Users, including the root user cannot delete the objects during a pre-defined retention period.
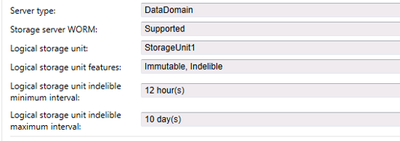
WORM enabled storage support is also available Data Domain and HP. Backup Exec now detects and notifies if the device is WORM capable, enabling customers to take full advantage of the retention lock feature.
The Backup Exec data lifecycle management (DLM) takes care of reclaiming the space only when the retention period is expired. Until then the data is protected, and it cannot be modified nor deleted. The retention lock and its period for the data images written to the Data Domain OST device can also be checked using the Data Domain storage server portal.
Summary:
In the dynamic landscape of data management and compliance, Worm-enabled backup emerges as a comprehensive solution for organizations seeking to fortify their data integrity. By combining the immutability of backup copies with robust governance controls, businesses can confidently navigate the complexities of regulatory landscapes and ensure the security of their most valuable asset—data.
As cloud technologies continue to evolve, embracing Worm-enabled backup is a strategic step towards building a resilient and compliant data protection strategy in the cloud.
For more technical knowhow refer here.
Steps to configure WORM enabled cloud deduplication device.
Hardware and Cloud Storage Compatibility List.
Visit our website to download a free trial and learn more about our products and services.
https://www.veritas.com/protection/backup-exec
Step by Step guide to download and install Backup Exec product and licenses.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Power-up ransomware resiliency with retention lock/WORM in Protection
- Anomaly Detection in Backup Exec in Backup Exec
- Ransomware Resilience in Backup Exec in Backup Exec
- Understand, Plan and Rehearse Ransomware Resilience series - Day 1 in Protection
- Understand, Plan and Rehearse Ransomware Resilience series - Design to Recover in Protection