- VOX
- Technical Blogs
- Protection
- Understand, Plan and Rehearse Ransomware Resilienc...
Understand, Plan and Rehearse Ransomware Resilience series - Access and Improve
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Quickly map your security assessment and find gaps that remain uncovered is a key to improve your security posture. And Veritas Appliance security meter can do this for you and also I included ten tips to do more!
To help you fully utilize the Veritas appliance zero-trust architecture, a security meter provides you with ONE GLANCE To View, and ONE CLICK To Configure the security settings. The Security meter can keep tracking security settings and show you a list of available security features with quick links to configure them. The security meter can be found at Flex Appliance landing page, only the admin user can view this feature.
To learn more about Veritas Appliances, check Veritas Appliance Security Guide.
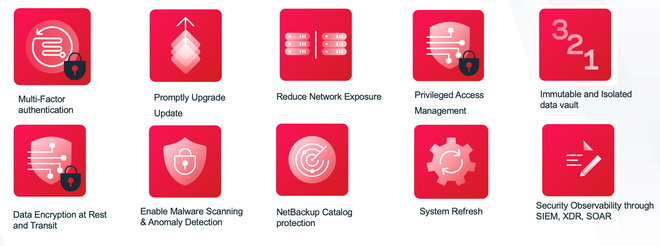
The Ten steps to increase your security posture
Ransomware uses stolen credentials to gain access to backup systems and then delete, encrypt or expire the backup data. For more details on how to enable these features, check Veritas NetBackup Appliance hardening guide.
Take the actions below to improve your cybersecurity stance to prevent attacks to backup and data protection systems.
- Enable Multi-Factor Authentication and elevate Veritas Appliance Security Level with Lockdown Mode.
The administrative credentials hold the keys to the kingdom. When the credentials are comprised, the attacker gets into backup systems and deletes your backups. Veritas Appliances gives unique protection from credential compromise with Lockdown modes and built-in OTP mechanism to prevent unauthorized access to the Operating System. Additionally, to protect Appliance WEBUI from unauthorized access, don’t forget to enable SAML SSO based MFA or smart card authentication.
- Keep All Systems and Software Updated
Don’t fight today’s ransomware with yesterday’s technology. Upgrade NetBackup and Appliance software to the latest releases to gain advantages from enhanced security features. Running out-of-date software can allow attackers to exploit security vulnerabilities. Veritas delivers monthly security patches to address critical vulnerabilities fixes.
- Reduce Network exposure by implementing Network Access Controls
Once ransomware enters an infrastructure, it spreads fast and purposefully increase the attack’s blast radius. One way to prevent such infection is to implement Network Access controls for your data and control plane. Network access control mitigates the risk of accessing information without the appropriate authorization. You can control which IP address or subnet can access Veritas Appliances via SSH and HTTPs with an allow list. All IP addresses not on the allow list are blocked by default. Should your credentials be compromised, attackers will not find a way to enter your backup infrastructure due to network access controls.
- Secure credentials with Privileged Access Management
IT administrators commonly share root, built-in accounts, and many other privileged credentials for convenience so workloads and duties can be seamlessly shared as needed. However, with multiple people sharing an account password, it may be impossible to tie actions performed with an account to a single individual. This creates security, auditability, and compliance issues. External hackers covet privileged accounts and credentials, knowing that, once obtained, they provide a fast track to an organization’s most critical systems and sensitive data. Don’t share or reuse credentials.
Veritas NetBackup and Veritas Appliance supports External password management solutions. You can deploy CyberArk Privileged Access Manager (PAM) to keep unauthorized users out, detect and stop threats in real-time. You can download Veritas Flex Appliance API (Availability, Protection, Insights) CPM Plugin. Do not forget to set unique passwords for built-in accounts to provide additional protection from stolen credentials.
- Immutable and Isolated data vault is not a choice and should be part of core backup Strategy.
Imagine few of your critical system are unavailable due to ransomware or sabotage from a disgruntled employee.
During the investigation you found that data was encrypted or deleted, and you’ll immediately think how I can gain protection from such attacks. Veritas NetBackup Appliances provides Immutable storage options with secure and encryption-resilient storage, so backup copies are tamper proof. Once immutability is enabled data no longer could be deleted or encrypted during ransomware attacks and that’s the key to cyber-recovery. It's time to revisit the old 3-2-1 rule - redundancy, geographic distance, and access. Three copies of your data - two on-site but on different media and one copy off-site. Leverage Veritas Recovery Vault solution for immutable and indelible off-site copy. 3-2-1 provides the protection you need from natural disasters. The rise in ransomware attacks calls for the extra “1” in 3-2-1-1 represents immutable storage.
- Enable Encryption
Its recommended best practice to enable encryption at rest and in flight. Encryption is specifically suited to thwarting data theft (leakage) and internal threats. If data is encrypted using robust industry standards, then even if data is stolen, it significantly reduces the attack exposure and safely ignore ransom demands. NetBackup Software provides various options to configure encryption. To ensure optimal security, NetBackup includes encryption features for data in rest and data in motion You can encrypt your data before you send it to the cloud. You can configure the KMS service from the NetBackup administration console or the NetBackup command line during storage server configuration.
- Enable Malware Scanning & Anomaly Detection
Malware and ransomware programs may go undetected on the target system for days, weeks, or months. These long durations make it quite likely that the malware will be backed up along with the regular backups. It is critical that organizations have malware scanning software to scan backups prior to recovery to find and eliminate malware before it is restored.
Veritas NetBackup provides unique built-in Anomaly detection and Malware Scanning helps to detect ransomware early on.
Once Malware scanning is enabled, please make sure critical events are fed to SIEM for alerts and security incident orchestration through platforms like Service Now.
- Enable NetBackup Catalog protection for both Primary and Media servers
Veritas strongly recommends protecting NetBackup catalogs by configuring dedicated policies during disaster recovery. Failure to backup the NetBackup catalog may result in data loss if a catastrophic failure occurs to the filesystems housing the various parts of the catalog. You can configure a dedicated catalog policy from NetBackup console to protect both Primary and media server catalog.
For Immutable storage, you can create shadow copies of catalog using CLI options available from MSDP shell interface.
cacontrol –catalog addshadowcopy /mnt/msdp/vol1
- Refresh your existing old generation of NetBackup Appliances with Next Generation Cyber resilient, Modern containerized and microservices based architecture like Flex or Flex Scale
Older servers and appliances that have seen five or more years of operation have a 3x greater chance of failure and unplanned downtime that might prevent your ability to quickly recover during ransomware attacks. Next generation of appliances provides cyber resilient and modern containerized microservices architectures with isolation capabilities for Airgap or Isolated recovery.
- Enable Security Observability through SIEM, XDR, SOAR Integrations
To detect and prevent threats, organizations need to promptly spot malicious insiders, compromised accounts, malware infections and other problem. With Flex Appliances, you can view the events at WebUI or forward syslog and audit logs including elevated shell commands to a syslog server or SIEM - Security information and event management. The logs have consistent timestamp formats which are necessary for accurate and efficient event correlations and log analysis.
SIEM, SOAR and XDR platforms are popular tools for combating unwanted trends and unsanctioned actions in IT ecosystems. NetBackup Audit messages can now be custom filtered and consumed by SIEM platforms by scanning the system log of the primary server, and digesting that information to provide reports, insights, and alerts. Automated response integration within NetBackup can automatically pause clients to stop any spread of undesired data, and SOAR integrations allow further customized actions based on triggers in the various categories of messages. NetBackup adds more capability to your ransomware response plans with insight and control with audit messaging.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Power-up ransomware resiliency with retention lock/WORM in Protection
- Anomaly Detection in Backup Exec in Backup Exec
- Ransomware Resilience in Backup Exec in Backup Exec
- Understand, Plan and Rehearse Ransomware Resilience series - Day 1 in Protection
- Understand, Plan and Rehearse Ransomware Resilience series - Design to Recover in Protection